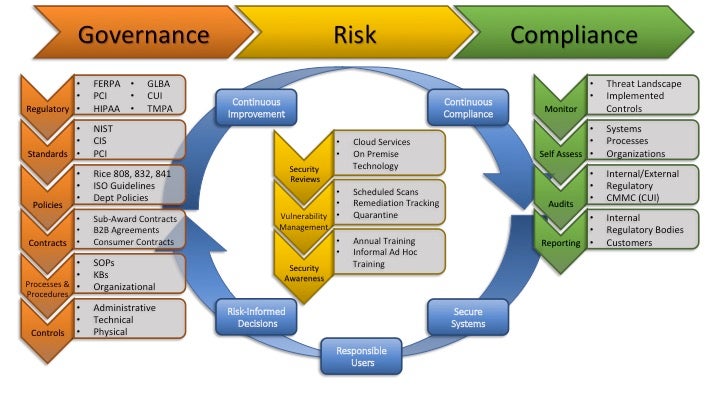
What is a Security or Standards Review?
Security reviews are a necessary collaborative process to attempt to quantify risks associated with an IT related service or application. It ensures that necessary controls are integrated into the design and implementation of these kinds of services at Rice. The Information Security Office regularly performs thorough, standards-based reviews that can help provide departments more visibility into areas of concern that may not be obvious or otherwise addressed from conversations with potential service providers. For example, our review process can help identify poor or missing vendor security practices. We can evaluate terms and conditions for a planned service or identify missing contract terms required for the kinds of data to be used. We are also able to identify and help draft departmental data handling procedures.
-
Sometimes we receive multiple requests at the same time. If you are implementing a solution that will contain sensitive or regulated data e.g. FISMA, HIPAA, FERPA, CUI, PCI data, please contact the ISO as early as possible in the project or initiative so that ample time is allowed to evaluate the services thoroughly.
-
Grants sometimes contain requirements for data handling called Data Use Agreements (DUAs) or may require compliance with Federal NIST standards such as Contolled Unclassified Information (CUI) or NIST SP 800-171. The Information Security Office is well acquainted with these standards and can guide you through the requirements.
-
To request a security review, email helpdesk@rice.edu.
What does the Review process look like?
Early identification and addressing of risk exposures will protect Rice's data, customer and end-user privacy, and ensure compliance with cybersecurity legislation and governance. There are a few steps to the review process.
-
Review Initiation - A request is made by a project team, department, or individual for a service to be reviewed.
-
Clarification - At this stage there may be follow up questions via email, questionnaires, or meetings scheduled to gather all relevant information for analysis of the service or services. This may also involve reaching out to vendors, third parties, or Rice partners and will be determined on an as needed basis.
-
Analysis Report - The ISO compliance team member will gather and analyze the information provided. Once potential risks have been identified, a Security Review Assessment will be completed and distributed to the person who requested the review.
-
Remediation & Risk Acceptance - The requester(s) can remediate or address any risks that are included in the report, working with the ISO and OIT if needed. All risks identified will be brought to the attention of the business sponsors, owners and executives requesting the given application/project. In the event that risks cannot be mitigated (reduced) or resolved (eliminated), the risk will need to be accepted by the CISO or CIO of the university.
For more on resolving risks to the university, please see our KB article: https://kb.rice.edu/102964
What are risk assessments?
Assessing risks and potential threats is an important part of running any organization, but risk assessment is especially important for IT departments that have control over networks and data. The purpose of IT risk assessment is to help IT professionals identify any events that could negatively affect their organization.
Our job is to identify risks and engage appropriate controls for reduction or elimination of:
- Loss of control to Rice data and IT services
- Loss of integrity to Rice data and IT services
- Accessibility to Rice data and IT services
What do we do?
The Compliance team works internally with various departments and groups within Rice to coordinate our activities. These include evaluating security controls, identifying and assessing risks, proposing risk reduction strategies, quantifying and scoring risks using a risk analysis process. Once the assessment is completed, the results are forwarded to ISO management for approval. If approved, the project is allowed to move forward. Occasionally the service does not meet the risk tolerance requirements and additional work is required. Groups we work closely with include the Office of General Council, Rice Compliance Office, Office of the Registrar, SPARC, Purchasing, and the OIT divisions Enterprise Applications and Project Management Office.
In addition, the compliance group also works internally with ISO on vulnerability assessments, risk analysis of software, service reviews, and deployments of equipment and services. We also help draft and maintain security policies and procedures.
How are risks assessed?
Weighing Risks and Controls
Upon receipt of a risk assessment request, the compliance team will assess the possibility of loss of control, loss of integrity, or loss of access to Rice data and IT services in the use of the service or system being assessed. The risks are identified and quantified. The data exposed in the service or system is evaluate and quantified. These factor are scored and weighed against the existing or proposed security controls to see how they compare. If the controls are on par or outweigh the risks, then the services is scored as moderate or low risk. If the risks outweigh the controls, the service or systems is scored as high risk. In all cases, the scoring is presented to management for review and approval or rejection. In some cases of rejection, the institutional decision makers can decide to accept a high risk. In such cases, there may be conditional approval. An example would be to accept a high risk for a short duration, or if it is deemed necessary to achieve a higher goal. Once a decision is made, the compliance team informs the service or systems owner of the outcome. If approval is granted, the service is documented and marked for annual review. If approval is denied, the service owner can discuss options with ISO.